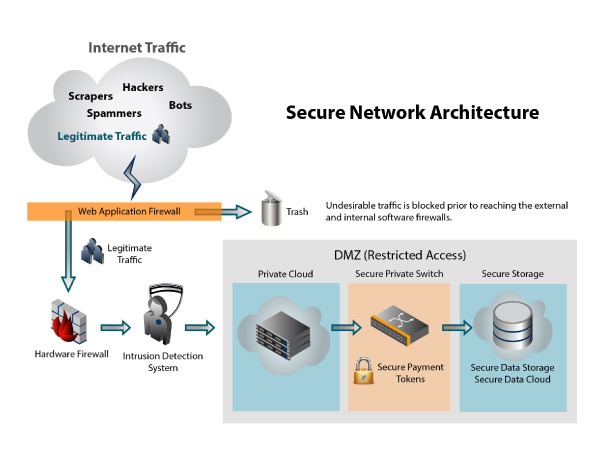
Gateway Security
uComm Transaction Gateway & Management was designed and implemented using industry best practices to achieve the highest possible availability and minimize risks associated with technology, network implementation, and managing the computing environment. It is built on a web services model, is PCI 2.0 compliant, and features redundant architecture for maximum fault tolerance and efficiency.
More detail regarding environmental security, gateway performance, and website security can be found with our Information for CIOs.
Fraud-Based Intelligence (FBI) Tools
uComm Transaction Gateway & Management is a transaction processing platform which offers best-in-class security, featuring FBI Tools. FBI Tools allow for a 360º view of security and provide maximum visibility for risk managers – ensuring they are the first, not the last, to know there is a potential threat. This comprehensive approach to risk management continually monitors each of the players’ activities and immediately alerts risk managers when vulnerabilities are identified. The vHub is designed to help answer the following questions:
- What business practices does the MERCHANT engage in that create risk? (ignorance, negligence, etc.)
- What is the PROCESSOR doing to manage risk?
- What is the common CONSUMER doing to add to a merchant’s risk? (unsafe computing, careless card handling, etc.)
- What is the CRIMINAL element doing to defraud merchants?
By monitoring each of the possible threat sources, FBI Tools enable a comprehensive, proactive approach to risk management. The tools provide visibility to and protection by:
- Monitoring MERCHANT business practices in real time
- Monitoring PROCESSOR practices in real time to determine whether or not policies are being enforced
- Incorporating security measures that assume the CONSUMER has made some mistakes
- Proactively defending against cyber crooks / CRIMINALS
More detail regarding what we are specifically monitoring is found on the Threat Monitoring page.